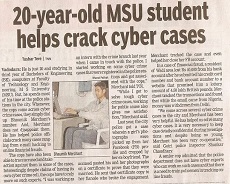
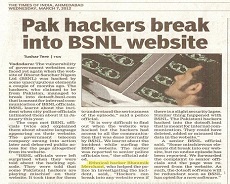
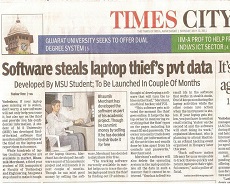
WOF(Walk on the Fire)
Today's requirement is to secure the Web Applications without changing the existing infrastructure.But at the same time, it is a big risk in case of WAF behaviour and false positives(legitimate traffic blocking). This article will demonstrate a new concept to evaluate any WAF without taking risk of putting it into inline mode. Everything will be in learning or in passive mode. This paper describes concept of one special engine, which can be used by the end user(website owner) to evaluate any WAF with zero risk ,no matter whether its vendor supports Passive mode or not(i.e. modsecurity or naxsi).